Juniper Contrail allows to configure the vRouter so that it mirrors traffic passing through a certain VMI towards a collector/analyzer which may implement DPI capabilities.
Setting up mirroring is pretty easy.
We use this very straightforward setup:
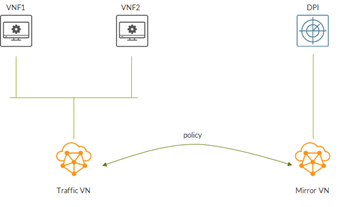
We have 2 VNFs attached to a virtual network called “Traffic VN”.
The DPI VM, called “DPI”, is attached to a second VN called “Mirror VN”.
We will mirror VNF1 traffic to the DPI VM.
Please notice, we did use Cirros VMs as VNFs and a Centos VM running tcpdump as DPI VM.
First, we create 2 virtual networks:
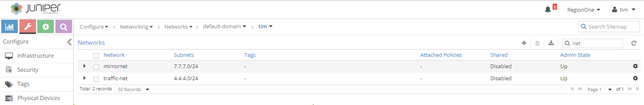
Virtual networks are standard L3 virtual networks, nothing unconventional.
We create our 3 VMs:
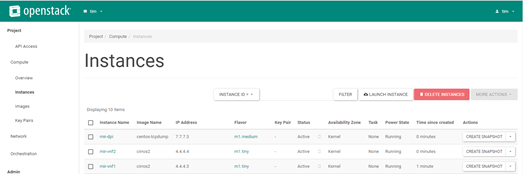
At this point we have:
- 2 VNFs on the 4.4.4.0/24 network that can talk to each other
- A DPI VM on the 7.7.7.0/24 network which can currently talk to its VN gateway only (no other VMs on this virtual network)
Now, let’s move to mirroring. Mirroring is configured at the VMI level. We tell contrail to mirror traffic going through a specific VM interface (VMI).
We enable mirroring on VNF1. The mirrored VMI has IP address 4.4.4.3.
We configure mirroring by editing the correct VMI under the “Ports” menu:
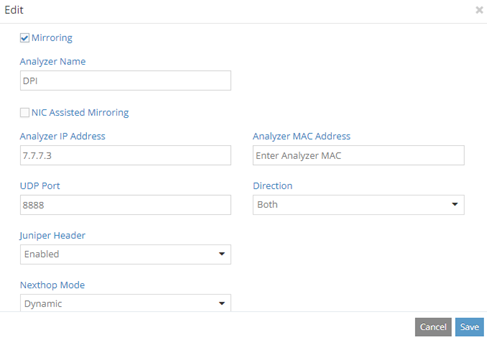
- Analyzer name is set to “DPI”; this is just a logical name
- Analyzer IP is DPI VM IP
- UDP port can be left blank or set to a particular value, for example 8888
- MAC can be omitted
- Juniper header is enabled
Packets will include the Juniper mirroring header:
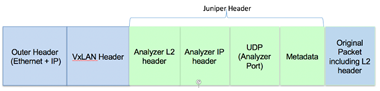
Metadata contain information about the originating virtual network.
Mirroring is ready.
Anyhow, VNF1 and DPI still cannot talk to each other as they are in different virtual networks. In order to overcome this, we configure a network policy:
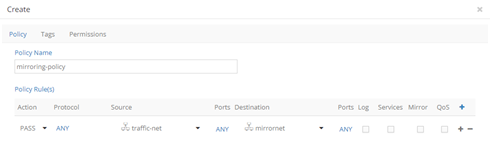
This policy has a single rule allowing any kind of traffic between Traffic VN and Mirror VN.
Next, we apply policy to virtual networks:

Now, everything is ready as we allowed communications between the two virtual networks.
Now, let’s connect to the compute node and access the vrouter agent docker. To do that run “docker ps” in order to detect vrouter agent container ID. Next run “docker exec -it bash”.
Find VNF1 VMI:
(vrouter-agent)[root@server-4c /]$ vif --get 15 vif0/15 OS: tapf8659136-11 Type:Virtual HWaddr:00:00:5e:00:01:00 IPaddr:4.4.4.3 Vrf:8 Mcast Vrf:8 Flags:PMrMtL3L2DEr QOS:-1 Ref:6 Mirror index 0 RX packets:438 bytes:25561 errors:0 TX packets:532 bytes:30040 errors:0 ISID: 0 Bmac: 02:f8:65:91:36:11 Drops:47 Ingress Mirror Metadata: 3 1e 64 65 66 61 75 6c 74 2d 64 6f 6d 61 69 6e 3a 74 69 6d 3a 74 72 61 66 66 69 63 2d 6e 65 74 ff 0 Egress Mirror Metadata: 4 1e 64 65 66 61 75 6c 74 2d 64 6f 6d 61 69 6e 3a 74 69 6d 3a 74 72 61 66 66 69 63 2d 6e 65 74 ff 0
Mirroring is enabled. This can be easily seen by looking at the flags; we have Mt and Mr that mean “Mirror transmit” and “Mirror Receive”.
We also learn mirror index is equal to 0.
We check mirror indexes:
(vrouter-agent)[root@server-4c /]$ mirror --dump
Mirror Table
Flags:D=Dynamic Mirroring, Hw=NIC Assisted Mirroring
Index NextHop Flags VNI Vlan
------------------------------------------------
0 129 D 0 0
And from there we get the next-hop index:
(vrouter-agent)[root@server-4c /]$ nh --get 129
Id:129 Type:Tunnel Fmly: AF_INET Rid:0 Ref_cnt:2 Vrf:-1
Flags:Valid, Udp, Copy SIP, Etree Root,
Oif:0 Len:14 Data:00 00 00 00 00 00 0c c4 7a 59 62 5c 08 00
Sip:192.168.200.11 Dip:7.7.7.3
Sport:8097 Dport:8888
Destination IP is 7.7.7.3, DPI VM IP as expected. Source IP is the compute node control+data IP. We can also easily spot destination port 8888, the one we had configured before.
Source port is set to 8097; anyhow, we will see multiple source ports as it is needed to open more than a session towards the DPI VM.
Finally, we start some traffic from VNF1.
On the DPI VM we enable tcpdump and filter to only capture UDP port 8888:
[root@mir-dpi ~]# tcpdump -nn -i eth0 udp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 13:00:33.252108 IP 4.4.4.3.64035 > 7.7.7.3.8888: UDP, length 132 13:00:33.252194 IP 4.4.4.3.63384 > 7.7.7.3.8888: UDP, length 236 13:00:34.252262 IP 4.4.4.3.64035 > 7.7.7.3.8888: UDP, length 132 13:00:34.252395 IP 4.4.4.3.63384 > 7.7.7.3.8888: UDP, length 236 13:00:35.252397 IP 4.4.4.3.64035 > 7.7.7.3.8888: UDP, length 132 13:00:35.252566 IP 4.4.4.3.63384 > 7.7.7.3.8888: UDP, length 236 13:00:36.252528 IP 4.4.4.3.64035 > 7.7.7.3.8888: UDP, length 132 13:00:36.252637 IP 4.4.4.3.63384 > 7.7.7.3.8888: UDP, length 236
As expected, we see traffic from the VNF1 VM. Destination port is 8888, the one we configured before.
The good thing about this design is that you have VNFs and DPIs on different virtual networks. This means that you could place a DPI on its own virtual network and have it receiving mirrored traffic from VNFs attached to different and multiple virtual networks.
In order to work, this requires a network policy for each virtual network that has to mirror traffic towards the DPI. Each network policy will involve the specific virtual network and the DPI virtual network.
Another great aspect is that mirroring is performed by contrail vrouter and does not require any configuration on the VM.
It is possible to be more granular and specify which traffic must be allowed.
For example, here, we make our policy more specific by only allowing UDP traffic with destination port 8888 towards the DPI VM:

Captured traffic can be saved into a pcap file and opened with Wireshark.
To see the actual packets it is necessary to tell Wireshark that UDP traffic towards port 8888 must be treated as Juniper mirrored traffic. This allows Wireshark to correctly decode the Juniper Header and the original packet which is contained inside it.
This is done by configuring Protocol preferences appropriately:

As a result Wireshark shows the mirrored packets. This image is taken from another setup (that is why we do not other adddresses).
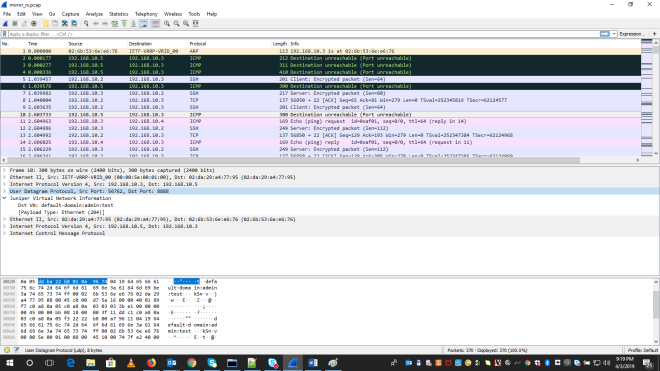
As you can see there are ICMP, TCP and SSH packets.
Moreover, we can easily spot the JUniper header containing the informatoin about the Juniper Header.
That’s everything about mirroring 🙂
Ciao
IoSonoUmberto